A reader on my blog tried to hack my account
Now all this time I've been teaching people how to hack Wireless networks, Windows machines, Websites and Social Networking accounts. All this we did in Kali Linux. For once, I'm moving away from the operating system and narrating a real life incidence of how someone almost got my Email account and password, and could have possibly infected me with a
RAT (remote administration tool). He didn't really mean to hack my account, but was rather interested in making a point. So this is how it happened.
How it started
Everyday, I check my blogger dashboard to see if there are any new comments on my blog. Today morning, I saw an anonymous comment (most of the comments are anonymous so that didn't alarm me) saying that the person needed my help with something but would only contact me via mail. I couldn't give him my personal mail address so I decided to use my website's mail instead, and sent him a message. This was his reply
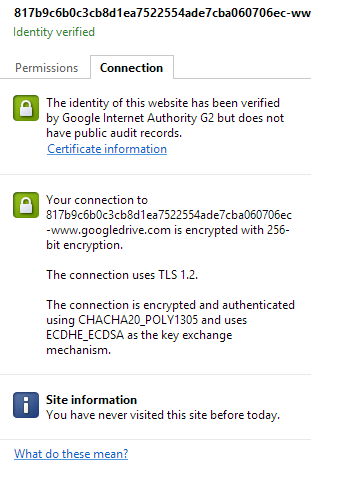
Looked fair enough. Out of curiosity I clicked the link and it took me to a google drive login page. Everything looked pretty convincing, and I could have easily entered my credentials into the login form, if it were not for the slightly suspicious URL. Also, it was https and chrome verified the digital certificates to be that of google. Faking this can be assumed to be next to be impossible. However, I still was cautious, considering that I run a hacking blog and it's not unlikely that a person visiting here might be good, maybe million times better than me.
What I did
So, I decided, I cannot just dismiss the page as phishing as such without trying. So I entered the email:abcd@gmail.com and password:lookslikephishing and pressed sign in. Now if it were a real page, it would have said incorrect password, but this page had no mechanism for verifying the form data, it actually just kept logging everything (i.e. it recorded whatever someone entered in the form) and would simply download the PDF no matter what we entered in the form. So, after entering the bogus login data, the PDF download started. It completed successfully and I ran the PDF. The content looked genuine and then I realized, well, what if this was a 2 fold attack, first phishing, followed by infection. He could have used a FUD remote administration tool which my antivirus wouldn't be able to detect. I have Windows Defender on my Windows 8 machine, but with proper crypting , anti-viruses can be evaded. So after this, I went to white hat section of hackforums and asked for help (
everyone needs help at some time or the other, and I suck at forensics and related stuff) . An expert analyzed my computer thoroughly via teamviewer, and the file was clean indeed. Meanwhile, the following mails had been sent to me.
Mails Recieved
 |
| He sent me some mails |
 |
| He knew I found out the phishing page thing |
 |
| He said he wants me to spread public awareness regarding this kind of phishing |
 |
| I replied to him saying that I'm finding out and cleaning the malware he sent me (if any). He replied and said he didn't send any malware or anything. |
Finally
I contacted him via FB. He turned out to be a fellow Indian and was even younger than me (I'm 17 he is 16). By this time I had finished my investigation, and the White hat expert from Hackforums didn't find anything either. I finally concluded that either there is no malware, or he's just too good. Latter is quite unlikely since he was not able to dig up my personal email address on his own. Believe me that's really easy to do. After having a conversation with him and doing some research on this HTTPS phishing page, I realized that it is done using a bug in Google drive, which has been discussed on
The Hacker News. I will see if I can replicate a HTTPS phishing website using this bug, and post a tutorial on how to do it. The sole intent of this post is to make people aware that Phishing is a real threat, and to encourage Google to fix this bug soon. Either ways, they will surely patch this bug after I write the tutorial on creating a Phishing page using Google Drive, as Google won't want it's user's accounts to be compromised by any random kid with a laptop who ended up on this website. Already they have applied a patch which makes carrying this out difficult and during the earlier days of this vulnerability, the URL was short and not suspicious at all, but now it's very long (see the screenshots). Update :
Google is probably not going to do anything about the issue as it is not a bug and I'm not gonna take the risk of writing anything which will usher upon me the wrath of Google (as I use blogger for hosting and blogger is owned by google). Google Drive, just like Dropbox allows hosting simple HTML sites like this phishing one. This can be abused, since some people will not know that this is a malicious document uploaded by someone and not a legit Google Drive login page, but it still is not a bug.  |
| Hacker's message on FB |
| After I told the hacker on Facebook about this post even he acknowledged that everything about this attack is perfect but the URL which earlier used to start with google drive now has a long suspicious prefix. The vulnerability has been half patched and google will possibly patch the remaining thing soon. |







No comments:
Post a Comment